Secure Platform Access with SAML 2.0 Authentication
Business Background
Single Sign-On (SSO) is an authentication process allowing a user to access multiple applications or services with a single login credentials. The primary goal of SSO is to simplify the user experience by reducing the need for users to remember and enter different usernames and passwords for each application they use within a particular system or across multiple systems.
SAML 2.0, which stands for Security Assertion Markup Language 2.0, is an XML-based standard for exchanging authentication and authorization data between parties, particularly between an identity provider (IdP) and a service provider (SP). SAML 2.0 is widely used for implementing SSO solutions, allowing users to log in once and access multiple applications or services without the need to log in again.
Some of the benefits of using SAML 2.0 are as follows:
- Single Sign-On (SSO): SAML 2.0 enables SSO, allowing users to log in once and access multiple applications or services without the need to log in again. This enhances user convenience and simplifies the authentication process.
- Security: SAML 2.0 provides a secure way to exchange authentication and authorization data between an identity provider (IdP) and a service provider (SP). Using XML-based assertions and digital signatures helps ensure the integrity and confidentiality of the transmitted data.
- Federated Identity: SAML 2.0 supports federated identity, allowing organizations to establish trust relationships between different systems. This is particularly useful when users need to access resources across organizational boundaries.
- Standardization: SAML 2.0 is a widely adopted industry standard, meaning many identity providers and service providers support it. This standardization promotes interoperability and simplifies integration between different systems.
Many identity providers support the SAML 2.0 protocol for SSO authentication. Here are just a few:
- Salesforce: Salesforce, a popular customer relationship management (CRM) platform, supports SAML 2.0 for SSO, allowing users to access Salesforce using their organization’s identity provider.
- Okta: Okta is a widely used Identity as a Service (IDaaS) platform that supports SAML 2.0 for secure and seamless authentication.
- Auth0: Auth0 is an identity and access management platform supporting SAML 2.0, among other authentication protocols.
- OneLogin: OneLogin is another cloud-based identity and access management solution that supports SAML 2.0 to enable SSO across various applications.
- Ping Identity: Ping Identity provides identity and access management solutions and supports SAML 2.0 for single sign-on capabilities.
- Azure Active Directory (Azure AD): Microsoft’s Azure AD, a cloud-based identity and access management service, supports SAML 2.0 for SSO integration with various applications.
This article explains how to secure the access of Titan Editors to the Titan Platform using SSO with SAML 2.0. To secure users’ access to published projects, please refer to this article.
Titan Solution
With Titan (as a service provider), you can configure secure Titan Platform access with SAML 2.0 authentication in a few clicks with different identity providers, for example, Salesforce.
How to Guide
Make sure that you are logged in to Titan with Account Owner credentials.
- The user’s email address in the identity provider must match the email address in Titan exactly.
- Make sure that the IDP’s SAML response includes the following user attributes:
- userId
- userName
- All fields are case-sensitive.
- Set up a new application or app manager in the identity provider.
- Make sure that you enable SAML as the sign-on method.
- Browse to the Titan Dashboard and click the Settings option.
- Click the Account Settings sub-option.
- Click the Configure button on the Login tile. The Platform SSO Configuration screen opens.
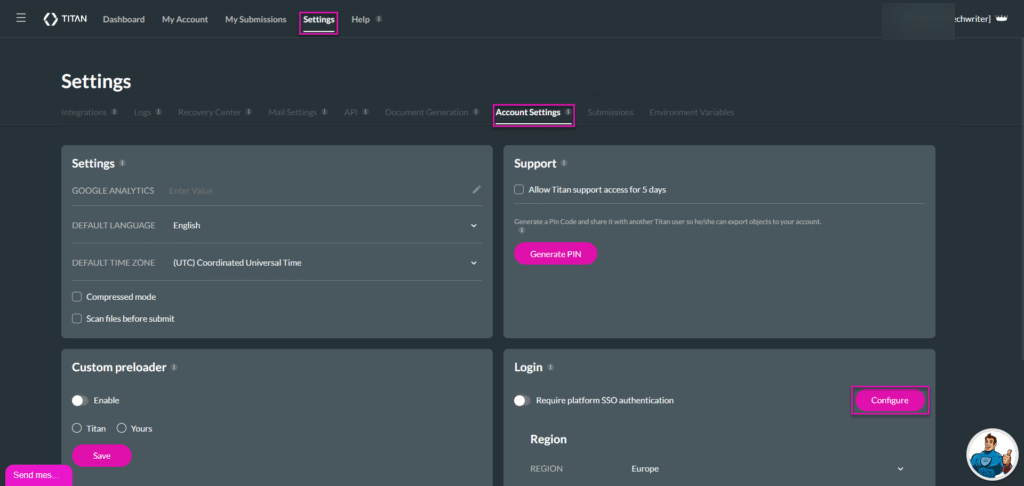
- Do the following on the Platform SSO Configuration screen:

- Copy the Access URL and paste it into the identity provider’s appropriate field.
- Copy the Service provider Entity ID and paste it into the identity provider’s appropriate field.
- If necessary, create a new IdP certificate or use an existing one. You will need the certificate details later.
- Save the identity provider app.
- Copy the IdP-initiated Login URL from the IdP app.
- Go back to Titan and paste the identity ID into the appropriate field.
- Copy the data from the IdP certificate and paste it into the Certificate field.
- Click the checkboxes as necessary:
- Do not force auth:
- When checked, and the user has an active session with the IDP, the user will be granted access to Titan without being re-authenticated by the IDP.
- When unchecked (default), even if the user has an active session with the IDP, the user will be forced to go through the IDP authentication process.
- Signed request:
- This option is not supported by all IDPs.
- For an IDP that does support this functionality, for instance, Salesforce, you can obtain a script from Titan to be updated in your Salesforce instance.
- Response to validation:
- This ensures a more secure connection that reduces the option to reuse the authorization to access the same resource (or page or URL) without revalidating with the IDP.
- Do not force auth:
The SSO login URL and Certificate fields are mandatory. You can also add the following optional fields:
- SSO Logout URL
- SSO Logout Redirect
- Click the Test button and then the Apply button.
- Use the Require platform SSO authentication toggle switch to enable the option if you are sure that the user’s email address in the identity provider matches the email address in Titan exactly.
For a practical example of how to do this with Salesforce as the identity provider, watch the following video:
Watch this video to learn more about configuring a secure Titan Platform access with SAML 2.0 authentication in Salesforce.
- 0:00 Learn how to configure login on the Titan platform with SSO.
- 0:42 Explore account settings.
- 1:13 See how to get the SSO login URL and the certificate.
- 2:18 Watch how to get Salesforce information.
- 2:34 An overview of creating a new connected app.
- 3:55 Learn how to get the Certificate and Key Management information.
- 4:41 View the saved app.
- 5:09 Watch how to paste the SSO login URL and the certificate in Titan.
- 5:47 See how to test the platform SSO configuration.
- 6:07 Find out how to enable the Require platform SSO authentication option in Titan.
- 7:09 Check out how to use the subdomain in the sign-in URL.
- 8:36 Discover incognito mode.
- 9:29 Learn how to add a collaborator who is not a user in Titan.

